Breadcrumb
Just what is Microsoft’s new Secured-core PC?
Microsoft today announced that it had been working closely with the major PC (including Panasonic) and chip manufacturers on security to create the most secure Windows device on the market. They call it the Secured-core PC and already it’s capturing a lot of attention. So just what is the Secured-core PC and why is it a critical development for businesses operating with highly sensitive data?
The Secured-core PC in a nutshell
Microsoft has partnered with its OEM partners to develop a new class of secure PC. Designed with deep integration between hardware and software and featuring the most advanced CPUs available, Secured-core PCs are intended to handle mission-critical data in some of the most data-sensitive industries. A Secured-core PC is a modern Windows device that comes with the highest level of hardware, software and identity protection ready right out-of-the-box.
Why is it needed?
As cyberattacks and threats become increasingly sophisticated, customers are looking for new solutions to provide them with more comprehensive security. This is particularly important in sectors where information is highly sensitive, such as the emergency services, defence or the public sector and for particular job roles, such as senior executives, R&D managers or mobile workers who carry important customer and company information on their device.
What does it do?
By deeply integrating hardware, firmware and the Windows operating system, Secured-core PCs protect against threats, with devices security rooted in hardware and guarded with secure, evolving cloud-based software to protect both data and identities.
A Secured-core PC enables users to boot securely, protect their device from firmware vulnerabilities, shield the operating system from attacks and prevent unauthorised access to devices and data with advanced access controls and authentication systems.
How does it work?
Secured-core PCs use hardware-based security components like Trusted Platform Module 2.0 (TPM) and modern CPUs along with virtualisation-based security (VBS) and Windows hypervisor code integrity (HVCI) service to create a secure, hardware-isolated environment that effectively isolates memory and critical components to prevent attacks and unauthorised access to critical parts of the operating system.
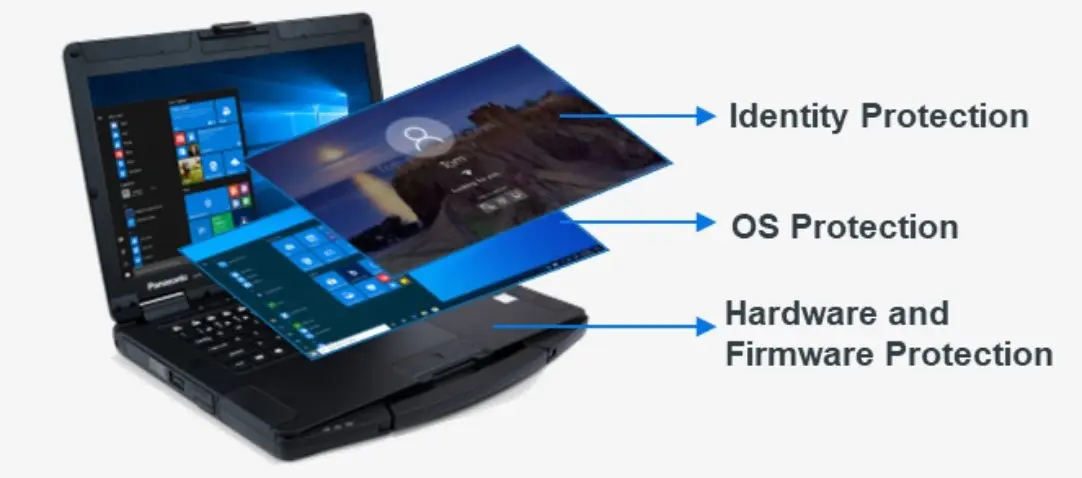
The Secured-core PC relies on advanced security capabilities built into modern CPUs to protect the integrity of Windows and its boot process from advanced attacks at the firmware level.
A secured-core PC uses dynamic root of trust measurement (DRTM) to launch the system into a trusted state by transferring control from the CPU directly to the Windows hypervisor loader via a secured and measured handoff. With the Windows hypervisor securely launched in a state measured by hardware, the VBS environment is then created in memory to isolate critical keys and processes from the regular Windows operating system that will soon be started. The hypervisor code integrity (HVCI) service is started in VBS which protects the Windows kernel by enforcing that all executable kernel code is signed by a trusted authority and by ensuring kernel code always allocates memory safely. This helps ensure that attacks are unable to inject malicious code into kernel mode processes and drivers.
All through the boot process a series of integrity measurements are made into the TPM 2.0 to securely record the chain of trust from the CPU to Windows. This process and data are isolated in TPM hardware to ensure that the measurements are not subject to tampering even if the platform was compromised. From here, the measurements are used to determine the integrity of the device’s hardware, firmware, and Windows boot components, thereby ensuring the device is free of persistent malware beneath the operating system.
Once Windows has started and is running securely and a user signs in with Windows Hello*, Credential Guard ensures that identity and domain credentials are isolated and protected in the VBS secure isolated environment thereby blocking credential theft attack techniques and tools used in many targeted attacks. Even malware running in the operating system with administrative privileges will not be able to extract authentication tokens.
Ultimately, Secured-core PCs are designed to protect against malicious access and malware through multiple layers of defence: a hardware-based root of trust, compartmentalised and isolated critical components, and certificate-based authentication.
Which devices are Secured-core PCs?
The Panasonic TOUGHBOOK 55 is one of the first Secured-core PCs and the first in the rugged Panasonic TOUGHBOOK range to offer this new level of security. As well as the latest security features, the TOUGHBOOK 55 is a semi-rugged notebook in a slim and unique 'honeycomb' design for improved strength and splash resistant design. In terms of flexibility, the TOUGHBOOK 55 is equally outstanding. It offers a huge array of configuration options, making it easier for customers to have exactly the device they want.
*To use Windows Hello with biometrics specialized hardware, including fingerprint reader, illuminated IR sensor, or other biometric sensors is required. Hardware based protection of the Windows Hello credential/keys requires TPM 1.2 or greater; if no TPM exists or is configured, credentials/keys protection will be software-based.
Take a look at the first Secured-core PC from Panasonic TOUGHBOOK.
Read more insights…
blog
How to Accelerate Your Business’ Migration to Windows 11
With Windows 10 reaching end‑of‑life in October 2025, organisations operating mobile devices that still haven’t upgraded are at a critical crossroads – and increasingly vulnerable to security risks. Teams must, therefore, quickly assess how they’ll make the decisive move to Windows 11.
article
Panasonic Connect Taiwan Factory Earns Prestigious RBA Platinum Certification
Panasonic Connect has announced that its key production site, Panasonic AVC Networks Taiwan Co., Ltd. (Panasonic Taiwan), has achieved Platinum status in the Responsible Business Alliance’s Validated Assessment Program (VAP) - the highest possible rating.
whitepaper
Whitepaper: Staying Competitive Through Smart Automation
Download the latest whitepaper featuring important European case studies that showcase how European manufacturers can stay globally competitive.
blog
A Transformative Year Ahead for Mobile Field Teams in 2026
Field teams in 2026 need edge AI, resilient connectivity, flexible procurement, and robust security. This is essential for boosting efficiency, protecting data, and modernising mobility strategies for smarter, safer field operations.
Sorry there was an error...
The files you selected could not be downloaded as they do not exist.
You selected items.
Continue to select additional items or download selected items together as a zip file.
You selected 1 item.
Continue to select additional items or download the selected item directly.
Share page
Share this link via:
Twitter
LinkedIn
Xing
Facebook
Or copy link: